Your website is more than just a digital space, it’s your brand, your business, and in many cases, your livelihood. But when it gets hacked, panic often sets in. Suddenly, your homepage looks different, your emails land in spam, or worse, your site is down completely.
The good news? A hacked website can be fixed. This guide breaks down how hacks happen, how to recognize them, and most importantly, how to recover and protect your site from future attacks.
What is a website hack?
Hackers may steal sensitive information, insert malicious code, redirect visitors to other websites, or even crash your site entirely.

Common Ways Hackers Break Into Websites
Hackers use different techniques to exploit vulnerabilities. The most common include:
Get TikTok SEO Cheat here
1. SQL Injection Attacks
This is one of the oldest and most common methods. Hackers inject malicious SQL code into web forms (like login fields) to trick your database into giving them access. With this, they can view, modify, or delete important data.
With SQL, you can create, retrieve, update, and delete database records. It is used for logging a user into the website and storing details of an eCommerce transaction.
Most times, these hackers involve the use of automated tools to perform SQL injections on remote websites. They set out to scan thousands of websites, testing many types of injection attacks until they are successful.
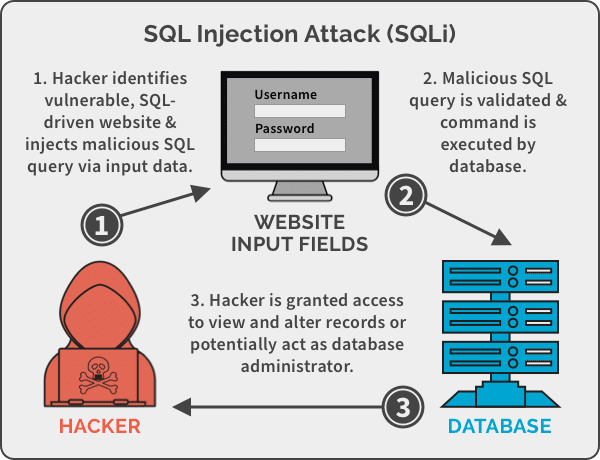
Prevention: Always sanitize and validate user input. Use prepared statements in your code to protect database queries.
2. Cross-Site Scripting (XSS)
Here, hackers embed malicious JavaScript into links or forms. When clicked, these scripts can steal user data, hijack sessions, or inject unwanted ads.
Another way hackers hack a website is the use of Cross-site scripting which is used to exploit the vulnerability of the website by hackers. It is one of the more difficult vulnerabilities to deal with because of its complexity.
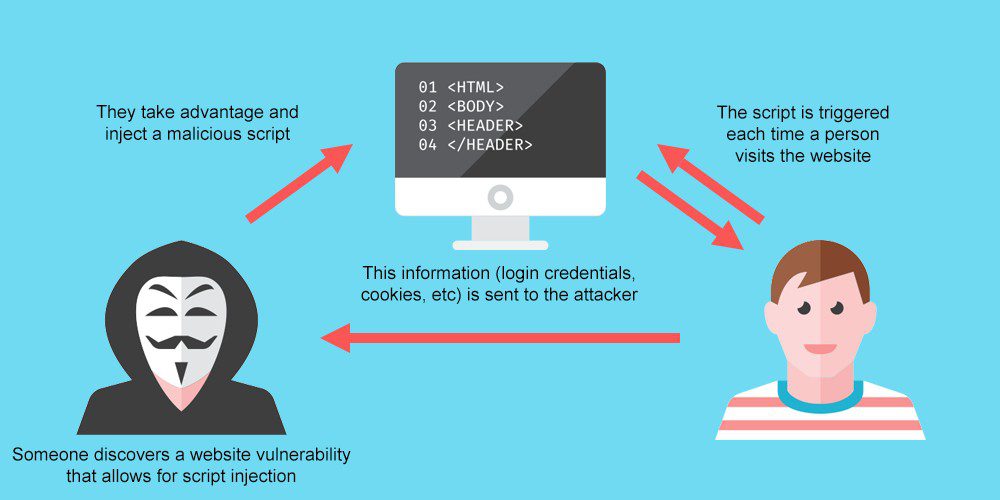
Where do they normally place these malicious links?
Most times hackers place these malicious links into web forums, social media websites, porn sites, and other prominent locations where users will click them.
Prevention: Filter all user inputs and strip out suspicious scripts before they run.
3. Denial of Service (DoS/DDoS)
Hackers flood your site with fake traffic, overwhelming your server until it crashes. This can make your website unavailable for hours or even days. Wikipedia
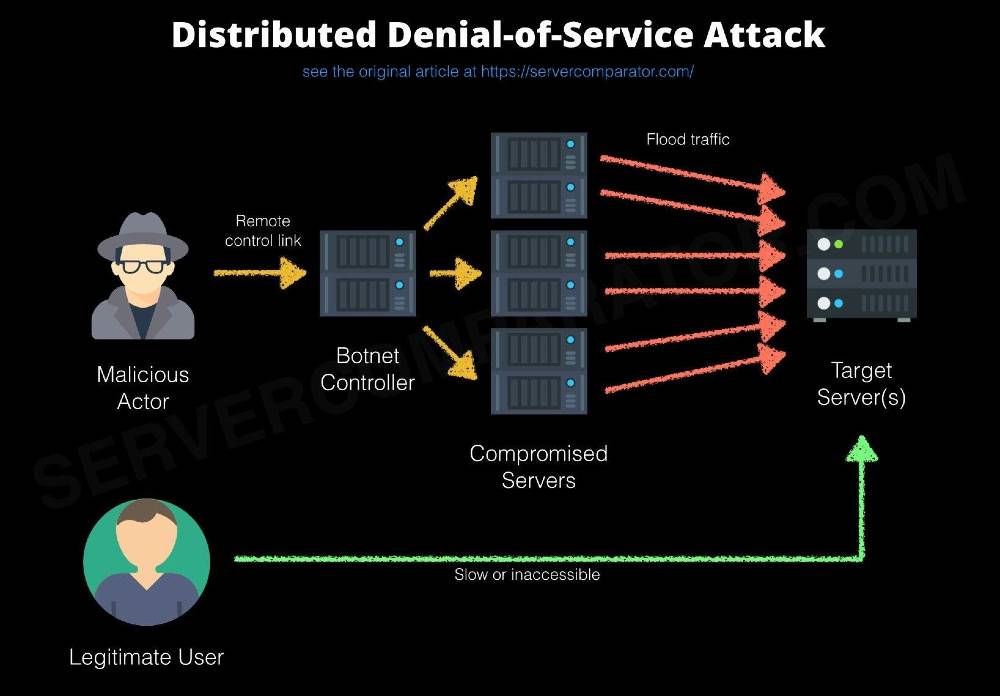
A denial of service attack floods a website with a huge amount of Internet traffic, causing its servers to become overwhelmed and crash. Funny enough we were faced with this problem some months back and before we could rectify it, we lost our site but we thank God for grace and we are back.
Most DDoS attacks are carried out using computers that have been compromised with malware. The owners of infected computers may not even be aware that their machine is sending requests for data to your website.
Denial of service attacks can be prevented by:
- Using third-party DDoS protection tools like Akamai, Cloudflare, VeriSign, Arbor Networks, or another provider.
- Add Rate limiting to your web server’s router.
- Ensure to add filters to your router to drop packets from dubious sources.
- Dropping spoofed or malformed packets.
- Setting more aggressive timeouts on connections.
- Using firewalls with DDoS protection.
4. Cross-Site Request Forgery (CSRF)
This trick forces users (often logged in) to perform actions they didn’t intend, like transferring funds or changing account settings.
This is a common malicious exploit of websites. The user is usually logged into the website, so they have a higher level of privileges, allowing the hacker to transfer funds, obtain account information or gain access to sensitive information.
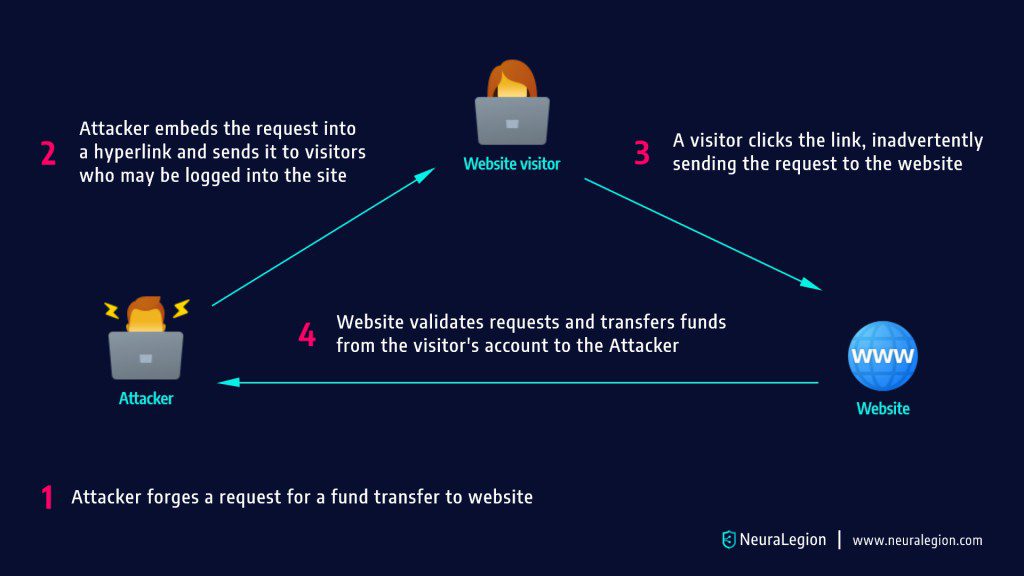
Prevention: Use CSRF tokens, verify request origins, and always validate session authenticity.
How CSRF Attacks Work
Hackers use hidden forms, AJAX, or image tags to send forged commands. Victims are unaware, and the website mistakenly treats the request as authentic.
Difference Between XSS and CSRF
- XSS: Does not require a user to be logged in.
- CSRF: Requires the victim to be logged in and trusted by the site.
How to Prevent CSRF
Websites can defend against CSRF by:
- Checking HTTP headers to verify request origins.
- Using CSRF tokens in web forms to confirm authenticity.
CSRF Prevention Measures That Do Not Work
- Using a secret cookie
All cookies are sent with every request, so they can’t guarantee the user’s intent. - Only accepting POST requests
Attackers can still trick victims into sending forged POST requests using hidden forms or scripts. - Multi-step transactions
If attackers can predict the sequence of steps, CSRF is still possible. - URL rewriting
This exposes the session ID in the URL, creating another security risk instead of solving the problem. - HTTPS
While essential for secure communication, HTTPS alone cannot prevent CSRF attacks.
5. DNS Spoofing (Cache Poisoning)
Hackers corrupt DNS data so visitors are redirected from your website to a fake, malicious one.
DNS spoofing, also known as DNS cache poisoning, is a hacking method where attackers insert false DNS records into a resolver’s cache. This tricks the server into sending users to the wrong IP address.
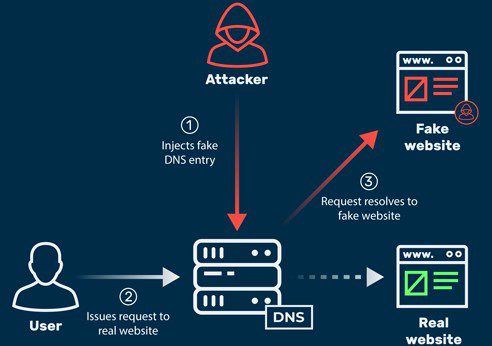
In most cases, it redirects traffic from a trusted website to a fake or malicious one designed to spread malware or steal data. Sometimes, attackers also use it to monitor and gather information about diverted traffic.
How to Prevent It:
- Use short DNS TTL (time-to-live) values.
- Regularly clear DNS caches on local machines.
- Consider using secure DNS services (like DNSSEC) for extra protection.
Prevention: Regularly clear DNS caches and use short TTL (time-to-live) settings.
6. Social Engineering (Phishing & Baiting)
Sometimes, the biggest security risk isn’t the system itself, it’s the people who use it. Social engineering is a hacking method that relies on manipulating users or administrators into giving away sensitive information, rather than breaking into a system directly.
Attackers use human psychology:— trust, curiosity, or even fear to trick victims into making mistakes that compromise security. Some common forms include:
Phishing
Hackers send fake emails or messages that look like they’re from a trusted source (like your bank or workplace). These messages usually contain links or attachments that trick users into sharing login details, personal data, or downloading malware. Once the attacker has this information, they can easily gain unauthorized access.
Baiting
This technique plays on curiosity. An attacker might leave a malware-infected USB stick or device labeled with something tempting (e.g., “Salary Data 2025” or “Confidential”) near a workplace. Once someone plugs it in, the malware executes and compromises the system.
How to Protect Against Social Engineering:
- Always double-check suspicious emails or links before clicking.
- Train staff and team members on spotting phishing attempts.
- Never use unknown USBs or devices.
- Use multi-factor authentication (MFA) to add an extra security layer.
Prevention: Train users to recognize phishing attempts and avoid suspicious downloads.
How to Know If Your Website Has Been Hacked
Not all hacks are obvious. Look out for these warning signs:
- Homepage suddenly changes without your approval
- On Search engine pages you may see different logo or name and also when the link is clicked it may redirect to porn/dating/gambling sites
- Browser or Google issues a security warning
- Hosting provider suspends your site
- Customers complain about strange activity
- Your site loads much slower than usual
- Emails from your domain land in spam
- Unwanted redirects or pop-up ads appear
If you notice any of these, it’s time to act fast.
Read also:
- Signs you need to change your web hosting
- How To Recover Hacked Facebook Account?
- How to shop safely online
- How To Block All Bank ATM Cards In Nigeria If Stolen/Lost With Code
- How to block stolen phone
- How to remove Privacy Protection Password (Anti-theft)
How to Fix a Hacked Website (Step-by-Step)
Here’s how to recover your site and regain control:
1. Flush DNS Cache
Clear your DNS cache to remove any malicious records.
- On Windows: open Command Prompt → type
ipconfig /flushdns→ press Enter. - Once cleared, refresh your site with Ctrl + F5 to load the correct version.
2. Scan & Restore Code Files
Hackers often inject malicious code into your site.
- Manually review your website files for suspicious changes.
- Use an FTP client to download and inspect key files (e.g.,
wp-config.php). - Restore clean versions of corrupted files from a backup.
3. Change All Passwords
Immediately reset every password connected to your site:
- Hosting account (cPanel, Plesk)
- FTP/SFTP
- Database (phpMyAdmin)
- CMS admin (WordPress, Joomla, etc.)
Use strong, unique passwords and avoid common usernames like “admin.”
4. Update CMS, Plugins, and Themes
Outdated software is a hacker’s best friend. Update your CMS (WordPress, Joomla, Drupal, etc.), plugins, and themes to the latest versions. Remove unused or suspicious extensions.
5. Backup Regularly
If you don’t already, start creating regular backups of your site. With a clean backup, you can quickly restore your site in case of future hacks. Use automated tools or your hosting provider’s backup service.
6. Secure the Comment Section
Hackers often inject code via comments. Add filters to block suspicious input and use plugins to moderate comments. Strip out HTML tags where possible.
7. Consider Switching Hosts
If your site keeps getting attacked despite fixes, it might be time to move to a more secure hosting provider. Look for one that offers built-in malware scanning, DDoS protection, and SSL support. So if you have been hacked, it is best to consider a new web hosting.
Best Practices to Prevent Future Hacks
- Install security plugins like Wordfence or Sucuri
- Use SSL (HTTPS) to encrypt data
- Limit login attempts to prevent brute force attacks
- Enable two-factor authentication (2FA) for admins
- Regularly monitor logs for suspicious activity
- Keep software, plugins, and themes updated
- Educate your team about phishing and online safety
Final Thoughts
Recovering from a hacked website can be stressful, but with the right steps, you can regain control and protect your site from future threats.
Remember: website security isn’t a one-time fix, it’s an ongoing process. Update regularly, back up consistently, and take proactive measures.
If your site has been hacked, don’t panic, act fast, follow the steps above, and turn this setback into a stronger, more secure future for your online presence.