There are some web owners who spoke about how their sites were hacked and do not know how to go about the recovery of their site. Well, this post deals with how to “Fix a Hacked Website” and get things on the go.
What is a website hack?
Websites hack is a situation whereby an unauthorized person or group of people have access to your website. This means they have access to information on your website without getting the required access or authorization from you.

How is website hack done?
A website hack is been done via the following process or method and they are called:
1. SQL Injection attacks
This method is one that involves the use of the Structured Query language (SQL) by Injection attack. It is the most common website hacking technique. We know that almost all websites use the Structured Query Language (SQL) to interact with databases.
With SQL, you can create, retrieve, update, and delete database records. It is used for logging a user into the website and storing details of an eCommerce transaction.
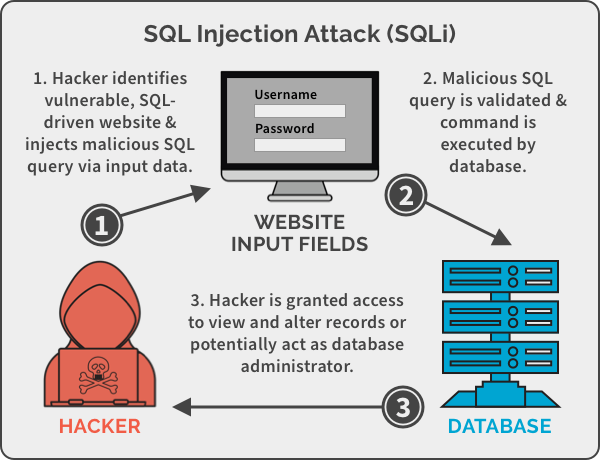
This method of attack places SQL into a web form in an attempt to get the application to run it. For instance, instead of typing plain text into a username or password field, a hacker may type in ‘ OR 1=1.
If the application appends this string directly to an SQL command that is designed to check if a user exists in the database, it will always return true.
With such authorization (illegal), the hacker gains access to a restricted section of a website. Other SQL injection attacks can be used to delete data from the database or insert new data.
Most times, these hackers involve the use of automated tools to perform SQL injections on remote websites. They set out to scan thousands of websites, testing many types of injection attacks until they are successful.
How can you prevent SQL Injection attack?
SQL injection attacks can be prevented by correctly filtering user input. Most programming languages have special functions to safely handle user input that is going to be used in an SQL query.
2. Cross-site scripting (XSS)
Another way hackers hack a website is the use of Cross-site scripting which is used to exploit the vulnerability of the website by hackers. It is one of the more difficult vulnerabilities to deal with because of its complexity.
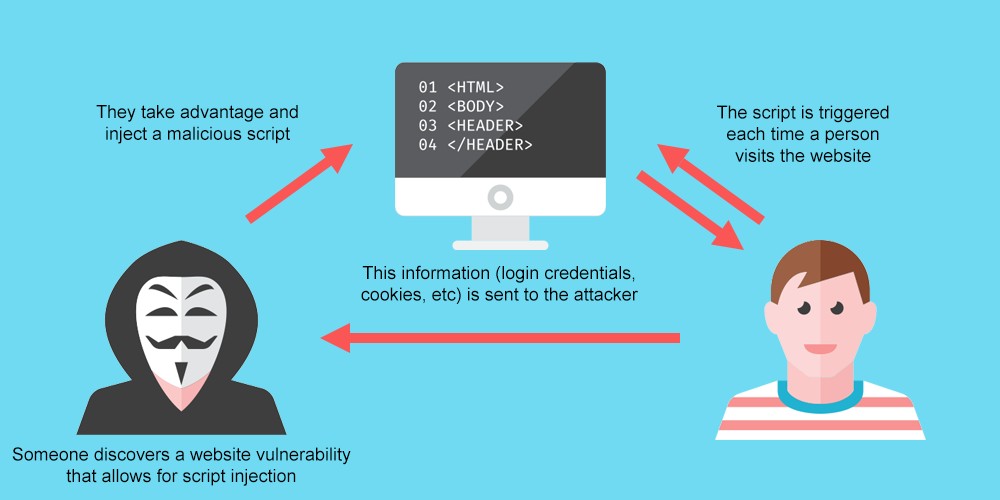
Some of the largest websites in the world have dealt with successful XSS attacks including Microsoft and Google.
This works when malicious Javascript scripts are embedded in hyperlinks. When the user clicks the link, it tends to steal personal information, hijack a web session, take over a user account, or change the advertisements that are being displayed on a page.
Where do they normally place these malicious links?
Most times hackers place these malicious links into web forums, social media websites, porn sites, and other prominent locations where users will click them.
How to avoid this XSS Attack?
To avoid XSS attacks, website owners must filter user input to remove any malicious code.
Read also:
- Signs you need to change your web hosting
- How To Recover Hacked Facebook Account?
- How to shop safely online
- How To Block All Bank ATM Cards In Nigeria If Stolen/Lost With Code
- How to block stolen phone
- How to remove Privacy Protection Password (Anti-theft)
3. Denial of service (DoS/DDoS)?
A denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting the services of a host connected to the Internet. Wikipedia
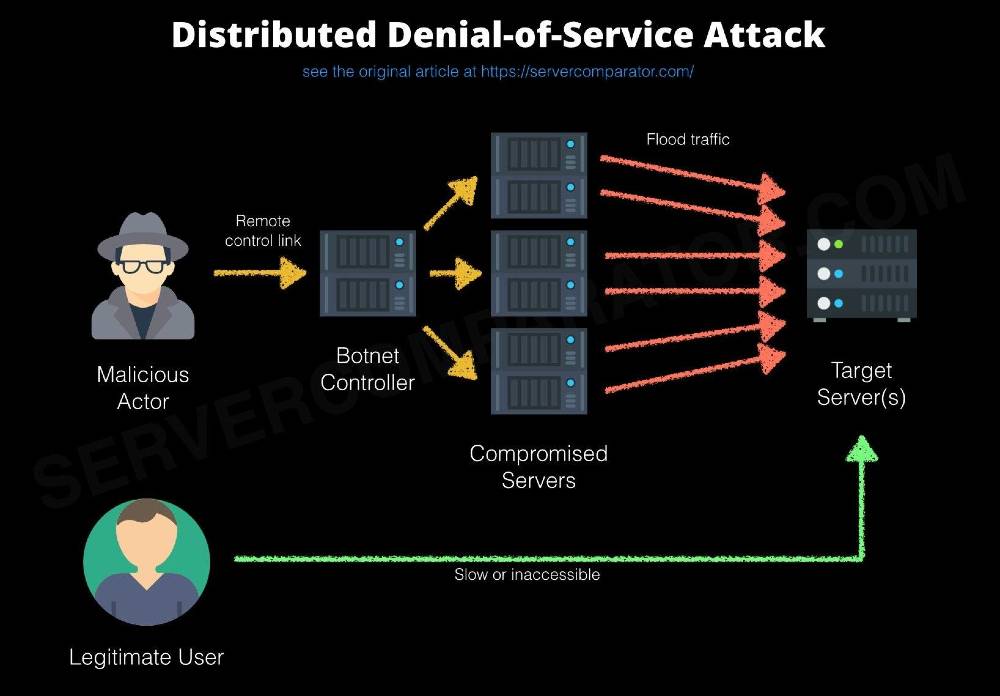
A denial of service attack floods a website with a huge amount of Internet traffic, causing its servers to become overwhelmed and crash. Funny enough we were faced with this problem some months back and before we could rectify it, we lost our site but we thank God for grace and we are back.
Most DDoS attacks are carried out using computers that have been compromised with malware. The owners of infected computers may not even be aware that their machine is sending requests for data to your website.
Denial of service attacks can be prevented by:
- Using third-party DDoS mitigation software like Akamai, Cloudflare, VeriSign, Arbor Networks, or another provider.
- Add Rate limiting to your web server’s router.
- Ensure to add filters to your router to drop packets from dubious sources.
- Dropping spoofed or malformed packets.
- Setting more aggressive timeouts on connections.
- Using firewalls with DDoS protection.
4. Cross-site request forgery (CSRF or XSRF)
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF or XSRF, is a type of malicious exploit of a website where unauthorized commands are submitted from a user that the web application trusts. Wikipedia
This is a common malicious exploit of websites. The user is usually logged into the website, so they have a higher level of privileges, allowing the hacker to transfer funds, obtain account information or gain access to sensitive information.
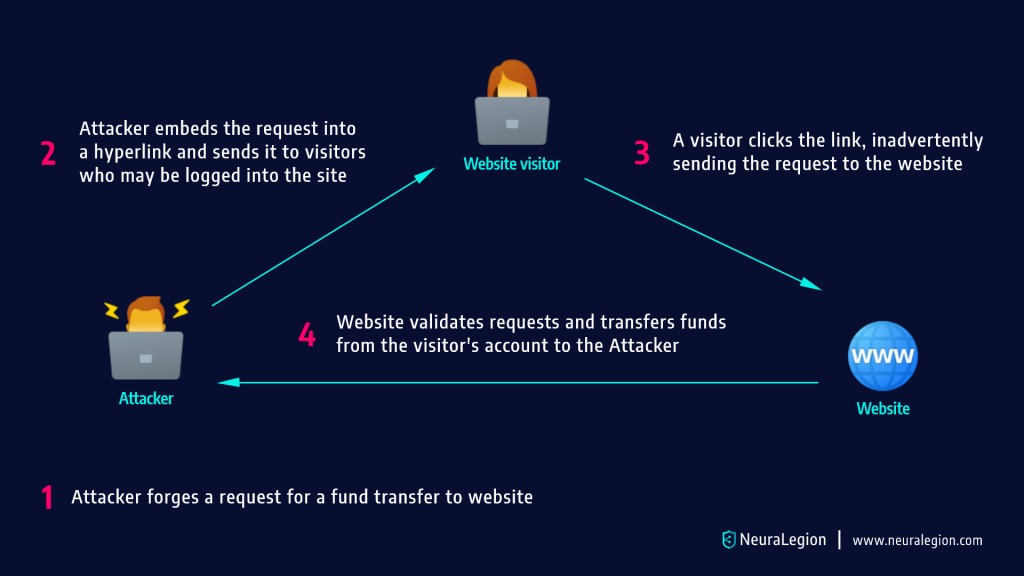
An attacker can use CSRF to obtain the victim’s private data via a special form of the attack, known as login CSRF. The attacker forces a non-authenticated user to log in to an account the attacker controls. If the victim does not realize this, they may add personal data—such as credit card information—to the account. The attacker can then log back into the account to view this data, along with the victim’s activity history on the web application.
There are many ways for hackers to transmit forged commands including hidden forms, AJAX, and image tags. The user is not aware that the command has been sent and the website believes that the command has come from an authenticated user.
The main difference between an XSS and CSRF attack is that the user must be logged in and trusted by a website for a CSRF website hacking attack to work.
Website owners can prevent CSRF attacks by checking HTTP headers to verify where the request is coming from and check CSRF tokens in web forms. These checks will ensure that the request has come from a page inside the web application and not an external source.
Prevention measures that do NOT work against CSRF
A number of flawed ideas for defending against CSRF attacks have been developed over time. Avoid these methods.
1. Using a secret cookie
Do you know that all cookies will be submitted with every request done? All authentication tokens will be submitted regardless of whether or not the end-user was tricked into submitting the request. Furthermore, session identifiers are simply used by the application container to associate the request with a specific session object. The session identifier does not verify that the end-user intended to submit the request.
2. Only accepting POST requests
Applications can be developed to only accept POST requests for the execution of business logic. The misconception is that since the attacker cannot construct a malicious link, a CSRF attack cannot be executed. Unfortunately, this logic is incorrect. There are numerous methods in which an attacker can trick a victim into submitting a forged POST request, such as a simple form hosted in an attacker’s Website with hidden values. This form can be triggered automatically by JavaScript or can be triggered by the victim who thinks the form will do something else.
3. Multi-Step Transactions
It has been observed that the Multi-Step transactions are not adequate prevention of CSRF. As long as an attacker can predict or deduce each step of the completed transaction, then CSRF is possible.
4. URL Rewriting
This might be seen as a useful CSRF prevention technique as the attacker cannot guess the victim’s session ID. However, the user’s session ID is exposed in the URL. We don’t recommend fixing one security flaw by introducing another.
5. HTTPS
HTTPS by itself does nothing to defend against CSRF. However, HTTPS should be considered a prerequisite for any preventative measures to be trustworthy.
5. DNS spoofing (DNS cache poisoning)
DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver’s cache, causing the name server to return an incorrect result record, e.g. an IP address. Wikipedia
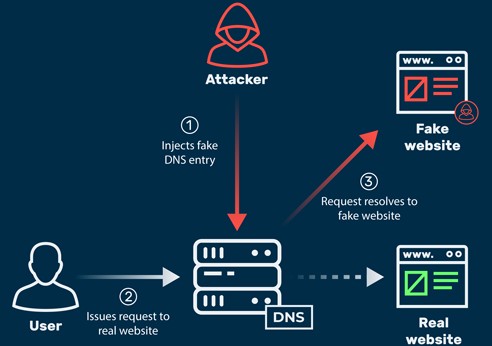
This website hacking technique injects corrupt domain system data into a DNS resolver’s cache to redirect where a website’s traffic is sent. It is often used to send traffic from legitimate websites to malicious websites that contain malware.
DNS spoofing can also be used to gather information about the traffic being diverted. The best technique for preventing DNS spoofing is to set short TTL times and regularly clear the DNS caches of local machines.
6. Social engineering techniques
One of the easiest ways to be hacked is through people who use a site. This method seeks to exploit weaknesses within the system. A hacker will convince/manipulate a website user or administrator to divulge some useful information that helps them exploit the website. There are many forms of social engineering attacks, including:
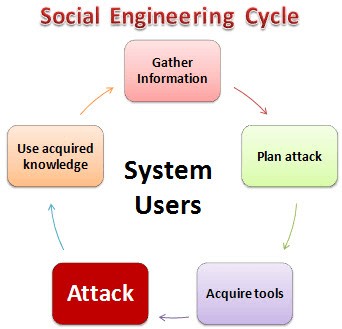
Phishing
This involves sending web users fraudulent emails that look like they are from the authentic website. The user is asked to divulge some information, such as their login details or personal information. The hacker can use this information to compromises the website.
Baiting
A hacker will leave a device near your place of business, perhaps marked with a label to entice you. When anyone in your organization uses such a device, it infects your device with malware and compromises it.
How can you know if your website has been hacked?
There are many ways to know if your website has been hacked and you can know if you notice any one of the following, then you should be able to identify that your website has been attacked. Here are few points enumerated on how to know your website has been hacked
- The homepage changed without notice
- The Browser Alerts You About The Hack
- Your Hosting Provider Takes The Site Offline
- Customers Contact You
- Google Flags Your Website
- The Site is Loading Slower than Usual
- Your E-Mails Are Sent to Spam
- Your Website Is Used for Unwanted Redirects or Advertisements
How to fix a hacked websites
Here are a few ways to fix this issue
1. DNS Flush
This helps you flush all DNS cache of the hacked website but does not restore your homepage. Hence, preventing any unauthorized person from using it or accessing it again.
Close all browser windows :- Click Start > All Programs > Accessories > Command Prompt. Type the following at the command prompt: ipconfig /flushdns. If the command was successful, you will see the message, “DNS Resolver Cache Successfully Flushed.”
When you see an error page when trying to access the homepage, try refreshing it with Ctrl + F5 several times until you see your home page come up. Use this method after you have restored your website back to its normal settings from the error page, this will give no room for any unauthorized person to get into your site again with their tactics.
You can find out how to do DNS flushing of any kind here
2. Get the Code File
There are two ways of finding out, either go through all the pages manually and check if they look correct or you can download the code file and then open it in notepad++ (this is a free text editor program used mostly by programmers).
This process involves restoring all the important files on your website back to how they were before it was hacked, this can be done by downloading wp-config.php which is located in the root folder of your website via an FTP client. If the wp-config does not look like how it was created then you should try restoring all other files back to their original position and state.
3. Change Passwords
The first thing to do is to change all passwords for the website including the FTP, PHPmyadmin, Cpanel. This will help you to remove the unauthorized person from the system. It also helps to prevent them from hacking a second time.
Ensure to change passwords to the wp-config.php file. Remove all plugins and themes that are not needed in your website before the attack occurred. Also, remove/ reset all other unnecessary programs.
4. Don’t use Generic Usernames.
Ensure to make things more difficult by making your username unique just like your password. Do not use things like “admin”, “administrator”, or “site owner”.
5. Keep Your Site Updated
The best way to avoid website hacking attacks is to ensure your content management system, plugins, and templates are all up-to-date. This way you will be more secured and rest assured that things won’t go out of hand.
6. Backup Your Site Regularly
Always backup your site. In a situation you experienced a hack, you can easily replace/restore back up. We had no backup and as such have to start all over but we thank God for his mercy’s endures forever. We are back and better.
7. Protect the Comment Section.
Validate the form input before any comment is accepted to strip out most HTML tags. Involve the use of keyword filters in WordPress to prevent any malicious code.
8. Consider Changing Hosting Company
When we had series of attacks on our website/blog, we got it back and it happened again. The best option was to switch to a more secured host and we opted for a foreign host. So if you have been hacked, it is best to consider a new web hosting.
Do we trust this post has been helpful? The best way to Fix a Hacked Website is to ensure you stay up to date with your theme and plugins or scripts. You can install security plugins like Wordfence, Sucurri, and others to help keep things secured. Kindly like, share, and repost this article to your social media network using the buttons below.
