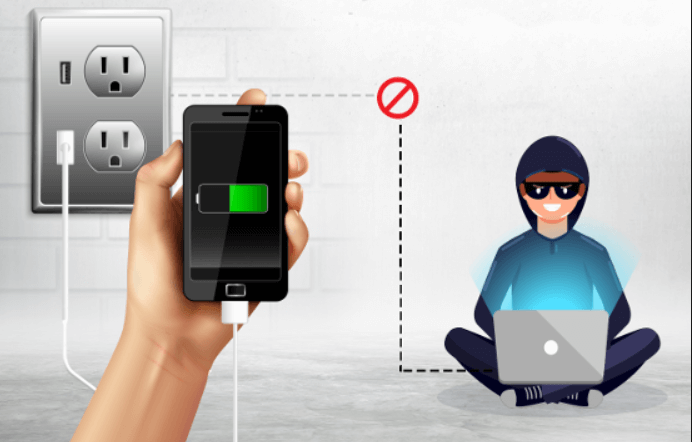
Did you know that simply charging your phone in public could put your personal data at risk?
Welcome to the world of Juice Jacking, a silent but dangerous cyberattack that turns public USB charging ports into tools for hackers.
Whether at an airport, café, bus stop, or hotel lobby, those convenient “free charging stations” could end up costing you far more than a full battery.
What Exactly Is Juice Jacking?
Juice jacking is a type of cyberattack where hackers use compromised USB charging ports or cables to steal data or install malware on your device.
It exploits one simple fact: USB cables carry both power and data.
When you plug into a hacked charging station, you unknowingly give attackers a bridge to your phone, allowing them to access your files, photos, messages, and even financial data.
Get TikTok SEO Cheat here
The concept is similar to ATM skimming, where criminals disguise malicious devices as legitimate machines. In both cases, the victim trusts the hardware and ends up compromised.
How Juice Jacking Works
When you connect your phone to a USB port, it’s not just drawing power — it’s also establishing a potential data connection. Normally, data transfer is turned off by default. But a compromised port can secretly activate data exchange between your device and a hidden system.
This means that while your phone appears to be charging, someone on the other end could be silently copying or injecting files into your device.
Types of Juice Jacking Attacks
There are several ways hackers can exploit USB ports in public spaces. Here are the four major forms:

1. Malware Installation
The attacker installs malware on your phone or laptop that can:
- Spy on your activities.
- Steal data and passwords.
- Lock your device (ransomware).
- Gain long-term control of your system.
2. Data Theft
This type silently copies your private files, photos, and documents.
If you stay plugged in for long, the hacker could even create a full backup of your phone — including contacts, messages, and login details.
3. Multi-Device Attack
Malware can spread from one infected device to another through connected cables or ports, turning multiple chargers or USB points into infected hubs.
4. Disabling Attack
Some malicious code locks you out of your device completely, giving hackers full access and sometimes demanding ransom for unlocking.
The Two Biggest Risks of Juice Jacking
1. Data Theft
Once your phone connects to a hacked USB port, the attacker can scan your device for banking details, stored passwords, or private messages. With this information, they can impersonate you online, access your financial accounts, or sell your data on the dark web.
2. Malware Installation
Through malicious apps, hackers can clone your data — including GPS locations, call logs, photos, and purchases. Some even freeze your phone and demand payment to restore access.
How to Protect Yourself from Juice Jacking
Knowing what juice jacking is isn’t enough — protecting yourself from it should become part of your daily digital safety habits. The good news is, you don’t need to be a tech expert to stay safe. Here are simple, effective ways to reduce your risk and keep your information secure anytime you charge your device in public.
1. Avoid Public USB Charging Ports
Public charging stations in airports, hotels, cafés, or malls might look convenient, but you can’t tell who installed or last tampered with them. Some could be modified with hidden data connectors that transfer information or inject malware the moment you plug in.
If your battery is low and you must charge, use an AC power outlet instead of a USB port. Bring your own wall charger and adapter so you know the connection is safe.

2. Always Use Your Own Charging Cable
It’s tempting to borrow a USB cable when you forget yours, but that single act can expose your entire phone. Some malicious cables, known as “spy cables,” are designed to record keystrokes, steal files, or transmit malware once plugged in.
Your best defense is to carry your own cable at all times — ideally one that you’ve purchased from a trusted brand or source.
3. Turn Off Data Transfer on Your Device
Most smartphones allow you to limit USB connections to “charging only.” This setting disables all data exchange between your device and the connected port.
To do this:
- On Android: Go to Settings → Connected Devices → USB Preferences → Charge Only.
- On iPhone: When you connect to a computer or unknown port, select “Don’t Trust This Computer.”
This small step can block hackers from accessing your phone’s internal data.
4. Lock Your Device Before Charging
When your phone is locked, it’s much harder for an external system to initiate data transfer or install malware. Always lock your screen before plugging it in anywhere.
Better yet, use Face ID, Touch ID, or a passcode to secure your phone. This ensures that even if a compromised port attempts to connect, the data access layer remains protected.
5. Power Off Before Charging in Public
Turning off your phone before charging adds an extra layer of safety. A powered-down device has limited interaction with the connected USB port, which reduces the risk of data exchange.
If you can afford to wait, power off your phone before connecting it to a charger you’re unsure about.
6. Carry a Power Bank
A portable power bank is one of the safest ways to keep your devices charged while traveling or on the go. It lets you recharge your phone anytime without depending on public ports.
Choose a power bank that suits your device’s battery capacity and keep it fully charged before leaving home — especially if you travel frequently.
7. Use a USB Data Blocker (USB Condom)
A USB data blocker — also called a USB condom — is a small adapter that fits between your charging cable and the port. It allows only electricity to pass through while blocking data pins entirely.
This means you can safely charge your device in public without worrying about hidden data transfers. They’re inexpensive, compact, and easy to carry — a smart investment for anyone who travels or works remotely.
8. Keep Your Software Updated
Manufacturers often release security patches to fix vulnerabilities that hackers might exploit. Always keep your phone’s operating system, antivirus software, and security apps up to date.
Regular updates strengthen your phone’s defenses and minimize risks from potential exploits, including juice jacking.
9. Be Cautious with Unknown Devices
Avoid connecting your phone to unfamiliar computers, kiosks, or shared devices — even for charging. Some of these systems can automatically initiate data transfers without asking for permission.
If you must connect to a public computer, make sure to select “charge only” mode, and never approve prompts asking for file access or trust confirmation.
10. Enable USB Restricted Mode (for iPhone Users)
Apple devices include a feature called USB Restricted Mode, which limits data access through the Lightning port after one hour of being locked.
You can enable this feature via:
Settings → Face ID & Passcode → USB Accessories → Toggle Off.
This ensures your iPhone’s Lightning port can’t be exploited unless the device is unlocked and authorized by you.
Pro Tip: Build Safe Charging Habits
Think of every charging station as a potential security checkpoint. If you develop the habit of carrying your own cable, charger, and power bank, you’ll never need to rely on unknown ports again.
Your phone holds sensitive details like bank apps, personal photos, conversations, and private work files. All of which can be stolen in seconds through a compromised charger. Staying vigilant is the easiest way to stay safe.
Stay Alert: Hackers Are Getting Smarter
Cybercriminals constantly invent new ways to exploit human behavior. Juice jacking might sound far-fetched, but it’s real — and growing as more public charging stations appear worldwide.
Whether their goal is to breach corporate networks or steal personal data, attackers rely on one thing: your trust.
Wrapping It Up
A full battery isn’t worth losing your privacy or your money.
Be cautious of where you charge your devices, and spread the word to friends, colleagues, and family.
By taking simple precautions — like using your own charger or a USB data blocker — you can stay powered up without powering a hacker’s attack.
Read Also: